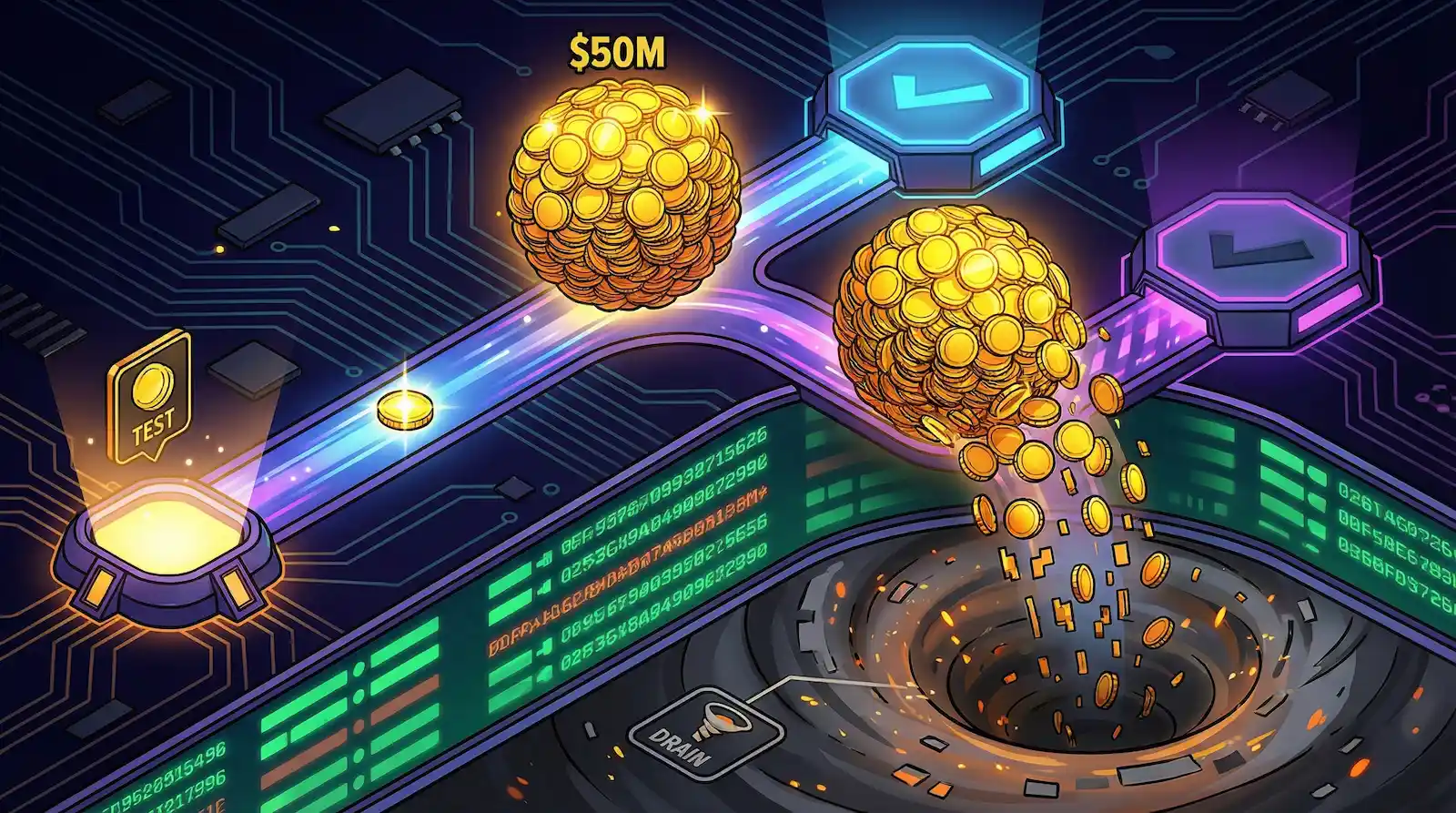
The victim first sent a $50 test to the correct address before the attacker’s look-alike address captured the full transfer.
- Scammer converted stolen USDT to DAI within minutes, blocking any potential Tether freeze action.
- Funds are being laundered via Tornado Cash, a mixing service that obscures transaction trails.
- Similar $70M address poisoning case in May 2024 resulted in 90% recovery after victim negotiated on-chain with attacker.
Dec. 20 (Crypto-News.net) – A crypto trader lost nearly $50 million in USDT after falling victim to an address poisoning attack on Dec. 19, with the stolen funds already converted to an unfreezable stablecoin and routed through mixing protocols.
The attacker drained 49,999,950 USDT from a wallet that had been active for two years and funded through Binance, according to security firm Web3 Antivirus. The victim had sent a $50 test transaction to the intended recipient address before transferring the full amount to a fraudulent look-alike address that the scammer had planted in the wallet’s transaction history.
Address poisoning works by sending small amounts of cryptocurrency from addresses designed to mimic legitimate ones. On-chain records show the scammer’s address shared the same first four and last four characters as the victim’s intended destination. The victim copied the spoofed address from their transaction history instead of the correct one.
Rapid Conversion Blocks Recovery
Within minutes of receiving the stolen funds, the attacker swapped the USDT for 49,533,438 DAI using a decentralized exchange. Unlike USDT, which Tether can freeze on-chain, DAI is a decentralized stablecoin with no central issuer capable of blocking transfers.
Tether has frozen over $2.7 billion in USDT to date in cooperation with law enforcement, but the rapid conversion left no window for intervention.
Funds Traced to Tornado Cash
The stolen funds are now being laundered through Tornado Cash, a mixing protocol that obscures transaction trails, according to blockchain analytics firm Arkham Intelligence.
The incident represents just one category of escalating threats facing crypto holders in 2025. While address poisoning exploits digital transaction histories, physical “wrench attacks” involving kidnapping and extortion have also doubled this year, demonstrating that criminals are targeting crypto wealth through both technical and violent means.
Recovery Remains Unlikely
The theft mirrors a May 2024 incident where a victim lost $70 million in wrapped Bitcoin to address poisoning. In that case, the victim successfully negotiated with the attacker using blockchain messaging, offering a 10% bounty and recovering approximately 90% of the funds.
However, with the current victim’s funds already converted to DAI and partially mixed through Tornado Cash, blockchain analysts consider recovery unlikely. The victim has not made any public statement.
Sources
Web3 Antivirus X Post – Original discovery, attack sequence details, victim wallet profile URL: https://x.com/web3_antivirus/status/2002043421368693140
Etherscan Transaction Record – Exact stolen amount (49,999,950 USDT), scammer address, fund conversion details, timestamp (Dec-19-2025 04:01:23 PM UTC) URL: https://etherscan.io/tx/0x40c3071839bcfba2623fe9e419bcaaf667b6570489d04d194f106282202de077
Arkham Intelligence Visualizer – Fund flow tracking, laundering pathway analysis URL: https://intel.arkm.com/visualizer/entity/0x7A1bEe3d53BF70861eF6C0652c63B206ea8fdE76
Protos Article – Attack methodology details, victim wallet provenance (2-year history, Binance funding), $70M prior case comparison URL: https://protos.com/crypto-trader-loses-50m-usdt-to-address-poisoning-scam/