Safety Detectives researchers found security flaws in Microsoft Defender, Windows’ built-in antivirus software, while investigating malware in an NFT game, according to a company report. The research, documented in the video “Microsoft Defender vs Malware: Is It Enough in 2024?”, revealed how the malware bypassed two-factor authentication (2FA) and compromised user systems, resulting in cryptocurrency theft of over $24,000.
The malware originated from an NFT gaming website offering monetary rewards for playing. Once downloaded, the game activated malicious software that hijacked the victim’s Google account, installed a disguised Chrome extension mimicking Google Keep, and circumvented 2FA. According to SafetyDetectives, the app’s technical documentation lacked transparency, raising red flags.
Using tools such as Wireshark, Process Monitor, and Process Hacker, the research team ran the infected application in a controlled virtual environment. During testing, Microsoft Defender failed to detect or block the malware as it downloaded suspicious files, accessed sensitive information, and gained administrative privileges without triggering an alert.
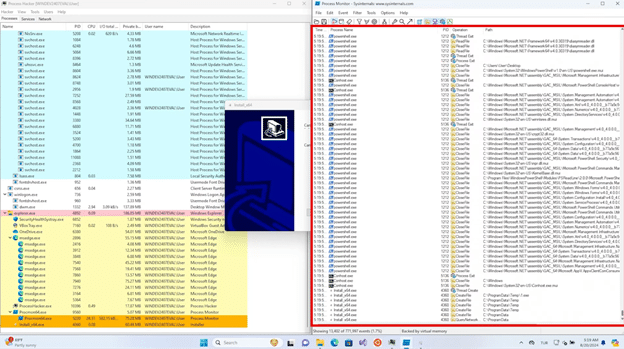
Subsequent tests with Bitdefender and Malwarebytes showed better results. Bitdefender intervened mid-execution when the malware attempted to access browsing history and login credentials, while Malwarebytes stopped the malware during the installation phase. Both solutions effectively prevented system compromise, with Malwarebytes responding faster.
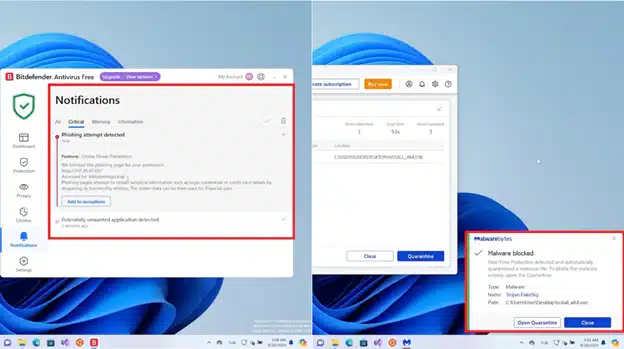
The investigation also revealed that the malware was programmed to avoid users located in Russia, Ukraine, and Belarus, indicating a likely origin in those regions. Additionally, the disguised Chrome extension could steal saved login data, monitor browser activity, and access all websites visited.
SafetyDetectives emphasized the importance of using robust antivirus software and exercising caution when downloading unverified applications. For further details and cybersecurity tips, visit SafetyDetectives’ Channel.

